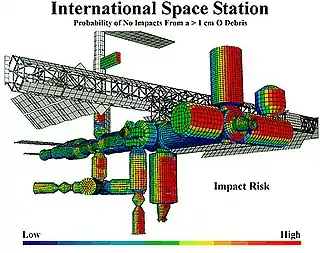
Risk analysis is the science of risks and their probability and evaluation.
Probabilistic risk assessment is one analysis strategy usually employed in science and engineering. In a probabilistic risk assessment risks are identified and then assessed in terms of likelihood of occurrence of a consequence and the magnitude of a potential consequence.
Risk analysis and the risk workshop
Risk analysis should be performed as part of the risk management process for each project. The data of which would be based on risk discussion workshops to identify potential issues and risks ahead of time before these were to pose cost and/ or schedule negative impacts (see the article on cost contingency for a discussion of the estimation of cost impacts).
The risk workshops should be attended by a large group, ideally between six and ten individuals from the various departmental functions (e.g. project manager, construction manager, site superintendent, and representatives from operations, procurement, [project] controls, etc.) so as to cover every risk element from different perspectives.
The outcome of the risk analysis would be the creation or review of the risk register to identify and quantify risk elements to the project and their potential impact.
Given that risk management is a continuous and iterative process, the risk workshop members would regroup on at regular intervals and project milestones to review the risk register mitigation plans, make changes to it as appropriate and following those changes re-run the risk model. By constantly monitoring risks these can be successfully mitigated resulting in a cost and schedule savings with a positive impact on the project.
Risk analysis and information security
The risk evaluation of the information technology environment has been the subject of some methodologies; information security is a science based on the evaluation and management of security risks regarding the information used by organizations to pursue their business objectives. Standardization bodies like ISO, NIST, The Open Group, and Information Security Forum have published different standards in this field.